考点
- Binwalk 分离
- 盲水印
- crypto 解密
- hashcat 爆破
- docx 隐藏文字
- bmp 隐写
解题过程
1. Binwalk 分离
拿到图片先进行 Binwalk 文件分析,可以看到有个 zip 压缩包,则 Binwalk 分离提取压缩包。
1 | 1:PNG image, 440 x 449, 8-bit/color RGB, non-interlaced |
2. 盲水印
进入压缩包后有wanan.png和舔狗日记.crypto两个文件,仔细看则会发现两个图片几乎一样,则容易联想到可能是盲水印。
使用随波逐流工具箱或者BlindWaterMark进行双图盲水印(key)解密,得到关键信息 1:ARJXU4MjE0。
wanan.png 为题目图片, wanan2.png 为解压后的图片。
1 | python bwmforpy3.py decode wanan.png wanan2.png out.png |

3. crypto 解密
.crypto文件使用Encrypto打开,输入前面获取的ARJXU4MjE0,得到三个文件舔狗日记1.docx、舔狗日记2.docx、最终我不想舔了.bmp.
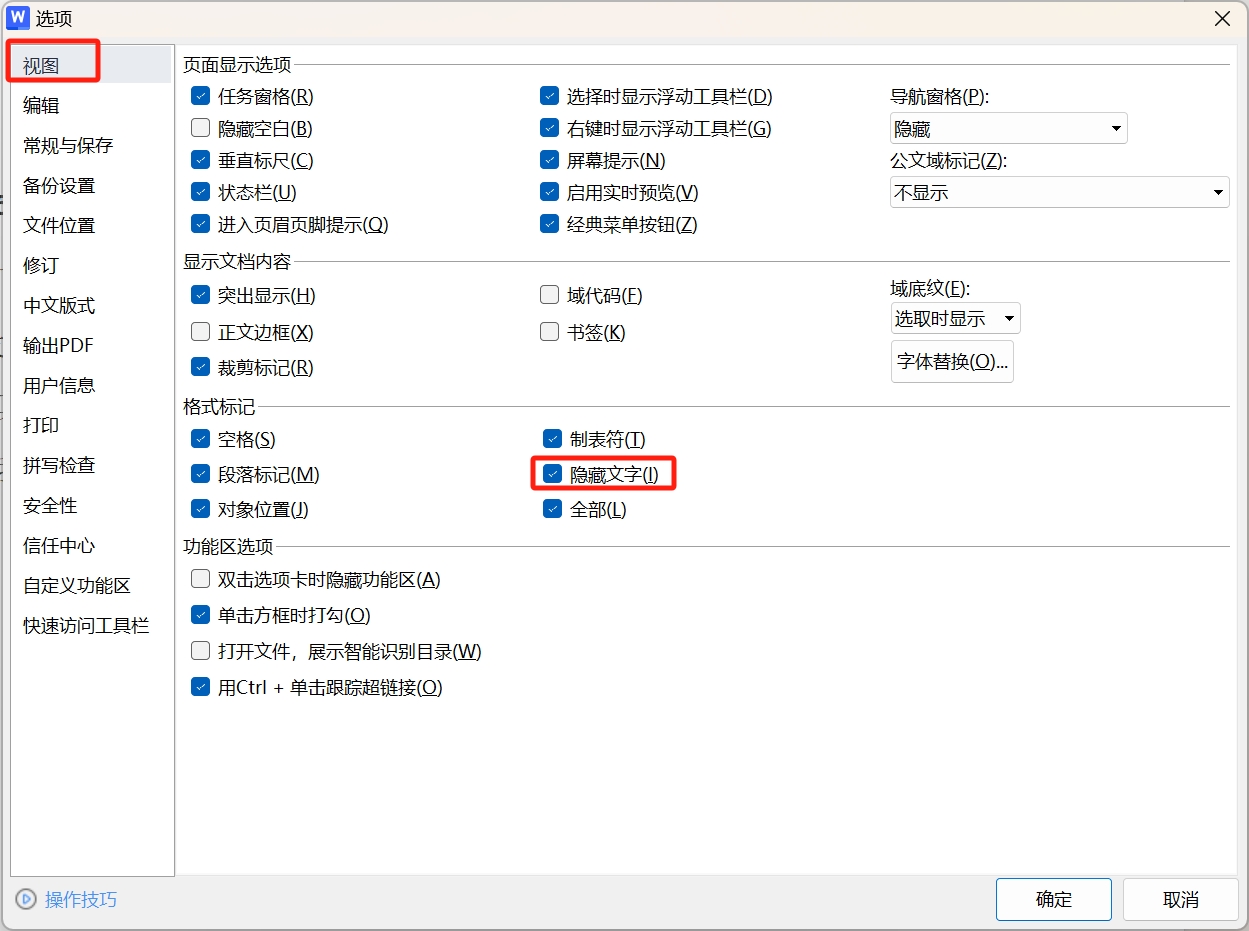
word 需要配置打开隐藏文字的格式标记,否则后面无法展示隐藏文字。
打开舔狗日记1.docx,全选文字颜色加深,发现没有异常,使用 Binwalk 文件分析,发现有异常的remember.zip。
Binwalk 文件分析
1 | 1:Zip archive data, at least v2.0 to extract, compressed size: 350, uncompressed size: 1432, name: [Content_Types].xml |
将该 word 文件后缀改为.zip后解压,拿到remember.zip。解压,打开里面的remember.txt,获取关键信息 2:那天,你告诉了我你最重要的8个数字,我记住了。
从中获取关键信息 3:8个数字
4. hashcat 爆破
打开舔狗日记2.docx,发现需要密码,再加上前面得知密码为 8 个数字。所以选择使用 hashcat 爆破 word 密码。
使用 hashcat 爆破前需要得到 hash 值,所以我们使用 Office2john 获取舔狗日记2.docx的 hash 值(文件路径不能有中文,需要改名)。
在john-1.8.0-jumbo-1\run目录下执行:
1 | python office2john.py 2.docx > hash |
获取文件 hash,打开删除前面的2.docx:,得到 hash
1 | $office$*2007*20*128*16*e8acb3ffadb859fcd9c0f38906f5a9b5*dc0a3deef00efb5fcdc115daa4784734*f97102e56fc53cf48fedba9a927e149d711928b2 |
可以看到是 2007 版本 office。
在 hashcat 文件夹下执行.\hashcat.exe --help | findstr Office,获得 office 的 Hash modes。
1 | 9400 | MS Office 2007 | Document |
2007对应9400的 hash 类型,使用 hashcat 爆破,得到关键信息 4:19990821。
1 | .\hashcat.exe -m 9400 hash -a 3 ?d?d?d?d?d?d?d?d -w 3 -O |
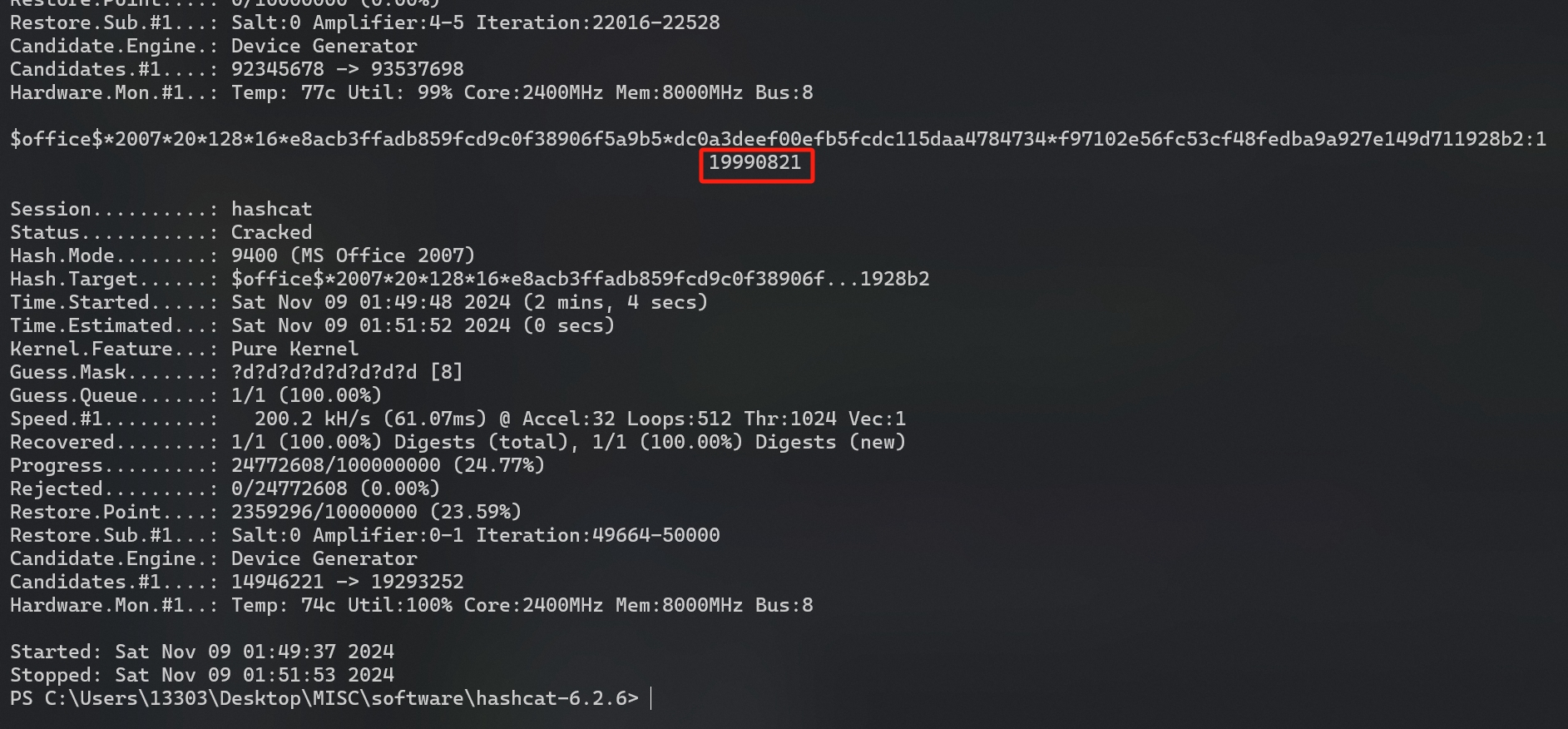
hashcat 同一个文件如果执行过的会保存记录,需要加
--show展示密码
5. docx 隐藏文字
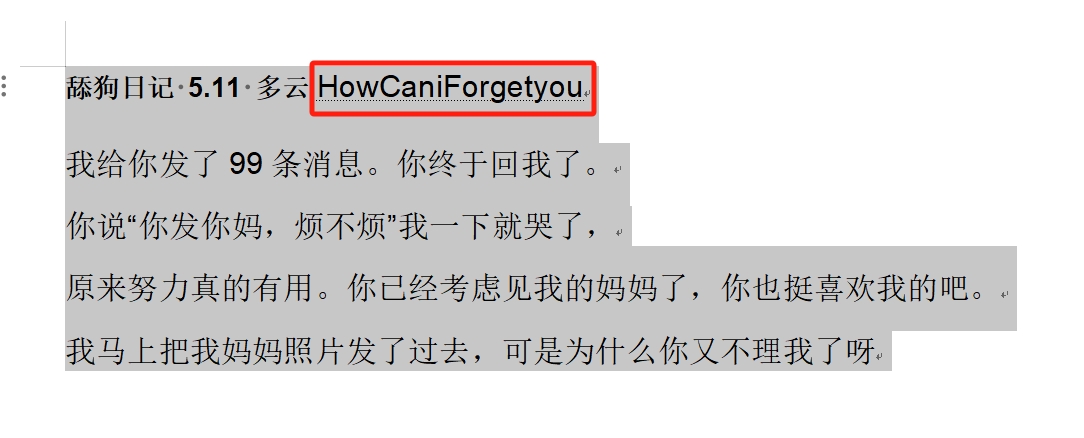
输入密码后,打开舔狗日记2.docx,全选文字,并且加深后,会发现出现隐藏文字,关键信息 5:HowCaniForgetyou。
6. bmp 隐写
还有一个 bmp 文件最终我不想舔了.bmp没有用到,推测为 bmp 隐写,我们使用软件wbStego4.3open,输入图片路径和密码,得到 txt 文件, 里面为最后的 flag:ACTF{Tr1edT0f0rgeTy0uBuTf1nallyTurnsT0f0rg1ve}。
此 flag:
Tr1edT0f0rgeTy0uBuTf1nallyTurnsT0f0rg1ve为 Leet speak 加密,解密为TriedToForgetYouButFinallyTurnsToForgive,意为尝试忘记你,但最终选择原谅。